NTU Cybersecurity Club Training Session 1#
In this lesson, we’ll explore fundamental networking concepts essential for cybersecurity. Let’s break down each topic:
- Types of Networks: We’ll learn about different network scales, from small personal networks (PAN) to massive wide area networks (WAN). Understanding these helps us identify potential security vulnerabilities at each level.
- TCP/IP Model: This is like the internet’s rulebook! It’s a simplified 4-layer model showing how data travels across networks. As cybersecurity students, we need to understand this because many attacks target specific layers of this model.
- OSI Model: Think of this as a more detailed 7-layer framework that helps us understand network operations. Each layer has its own security concerns - from physical security at Layer 1 to application security at Layer 7.
- Packets and Ports: This is where we learn how data actually moves across networks. Packets are like digital envelopes carrying our data, while ports are like specific doors where this data enters and exits. Many cyber attacks, like port scanning or packet sniffing, target these components.
Understanding these concepts is crucial because they form the foundation of network security. As future cybersecurity professionals, you’ll need to protect networks at all these levels.
Type of Networks#
- Local Area Network
Eg School Server Intranet
- Personal Area Network
Eg Bluetooth connection between phone and Airpods
- Wide Area Network
Eg The internet
Wireless Local Area Network
Eg Home Wifi Network
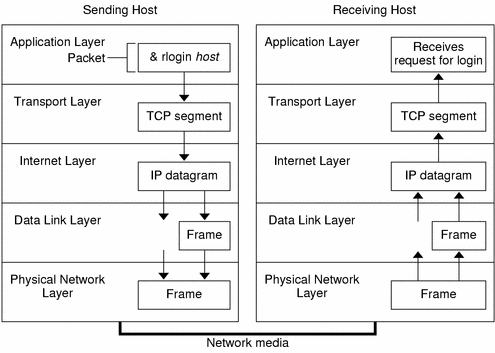
TCP/IP Model#
Think of the TCP/IP model as a postal service for the internet! It has 4 layers that work together to deliver your data:
- Application Layer (Top): This is like the post office counter where you drop off your letter. It’s where your web browsers, email clients, and other applications interact. For example, when you type “www.google.com”, this layer handles that request.
- Transport Layer: Think of this as the postal service’s sorting facility. It makes sure your data (like your letter) gets delivered correctly and in the right order. TCP ensures reliable delivery (like certified mail), while UDP is more like regular mail - faster but less guaranteed.
- Internet Layer: This is like the logistics network that decides the best route for your letter. IP addresses work like postal addresses, helping your data find its way across the vast internet. Just as a letter travels through different cities, your data packets travel through different networks.
- Network Access Layer (Bottom): This is the actual physical transportation - like the delivery trucks and roads. It deals with the hardware: the cables, wifi signals, and network cards that physically move your data.
An example: When you send a message on WhatsApp:
- Application Layer: WhatsApp prepares your message
- Transport Layer: Breaks the message into manageable chunks
- Internet Layer: Adds your friend’s IP address
- Network Access Layer: Converts your message into electrical signals to travel through cables or wifi
Understanding this model helps you grasp how internet communication works and where security measures need to be implemented!
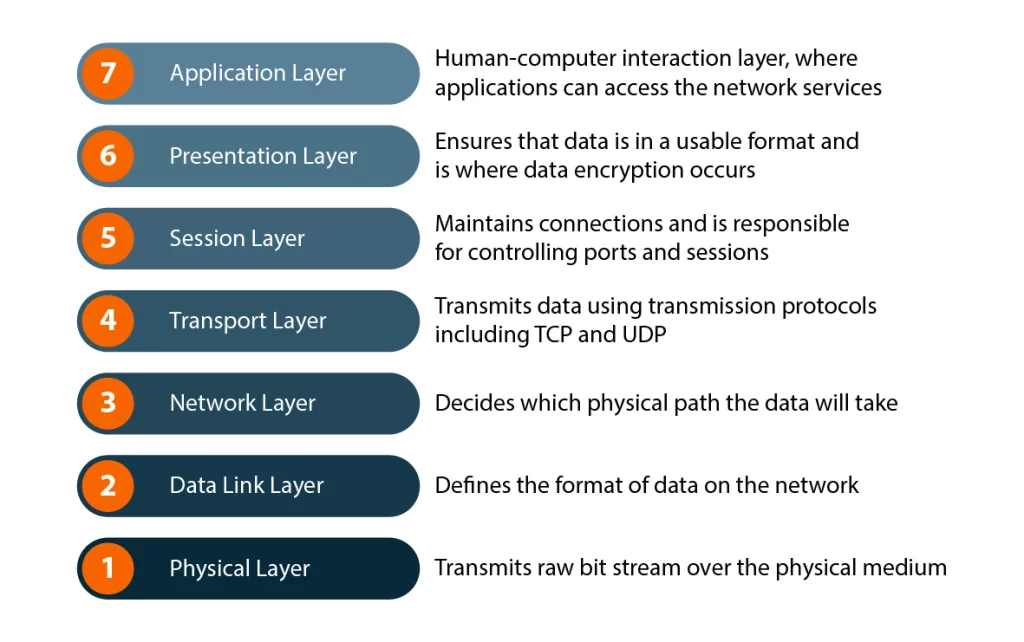
OSI Model#
The OSI (Open Systems Interconnection) Model is like a 7-layer cake that describes how computer networks work. Let’s break it down from top to bottom:
- 7. Application Layer: This is what you directly interact with - your web browsers, email clients, and chat apps. It’s like the user interface of the network.
- 6. Presentation Layer: Think of this as the translator. It handles data formatting, encryption, and compression. For example, it converts your JPEG images or encrypts your sensitive data.
- 5. Session Layer: This layer manages your connections. It’s like a phone call - it sets up, maintains, and terminates conversations between computers.
- 4. Transport Layer: Similar to the TCP/IP model’s transport layer, it ensures data arrives completely and in order. It’s like tracking a package delivery.
- 3. Network Layer: This handles addressing and routing - deciding the best path for your data to travel. It’s like a GPS for your data packets.
- 2. Data Link Layer: This layer deals with direct point-to-point delivery. It’s like the postal worker who handles the final delivery to your neighbor.
- 1. Physical Layer: The bottom layer represents the actual hardware - cables, wifi signals, and network cards. It’s the physical infrastructure that carries your data.
A simple way to remember the layers is the mnemonic “Please Do Not Throw Sausage Pizza Away” (Physical, Data Link, Network, Transport, Session, Presentation, Application).
Each layer has its own protocols and security concerns. For instance:
- Application Layer vulnerabilities include SQL injection and XSS attacks
- Transport Layer issues might involve TCP hijacking
- Physical Layer security could mean protecting against cable tapping
Understanding this model helps you identify where network problems occur and how to implement security measures at each layer.
Packets and Ports#
Packets#
Let’s break down an IP packet structure in a way that’s easy to understand! Think of it like a digital envelope with two main parts:
1. Header (The Envelope)#
- Version (4 bits): Like a postal code format - tells us if it’s IPv4 or IPv6
- Header Length (4 bits): Tells us how long the header is, like the size of the envelope
- Source IP Address (32 bits): Like the return address on an envelope
- Destination IP Address (32 bits): The delivery address where the packet needs to go
- Time to Live (TTL) (8 bits): Like an expiration date - prevents packets from circling forever
- Protocol (8 bits): Indicates what type of data is inside (TCP, UDP, etc.)
2. Payload (The Letter)#
This is the actual data being sent - could be part of an email, a webpage, or any other internet data. The payload can be up to 65,535 bytes!
A fun analogy: If the internet was a postal service:
- The header would be all the information written on the envelope
- The payload would be the actual letter inside
- TTL would be like “please destroy if not delivered within X days”
When you’re browsing websites or sending messages, your data gets split into these packets, each with its own header, and reassembled at the destination - kind of like sending a long letter as multiple postcards!

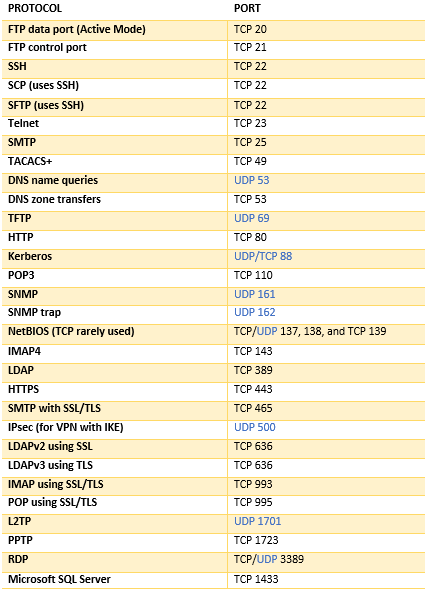
Ports#
Think of ports as apartment numbers in a building, where the building is your computer’s IP address. Just like how a building can have many apartments, your computer can have multiple applications receiving data through different ports.
Here’s how it works:
- Port Numbers: Each port is identified by a number (0-65535), just like apartment numbers. For example, web traffic typically uses port 80 (HTTP) or 443 (HTTPS)
- Application Assignment: Different applications “listen” on specific ports. When you run Discord, Spotify, and Chrome simultaneously, they each use different ports to receive their data
Common port examples you’ll encounter:
- Port 80: HTTP (regular web browsing)
- Port 443: HTTPS (secure web browsing)
- Port 22: SSH (secure remote access)
- Port 25: SMTP (email)
Understanding ports is crucial because:
- They’re often targets for cyber attacks (port scanning)
- You’ll need to configure them when setting up servers or network applications
- They’re essential for firewall rules and network security
VM Setup#
What is a VM?
VM means Virtual Machine, think computer within computer
Why VM?
- It allows us to have an isolated operating environment to go crazy and play with dangerous things like malware and viruses without worrying about affecting our main systems
- Additionally, we can use multiple different OS without having to change our computers!
Kali Setup#
https://www.youtube.com/watch?v=sAMnXte56yY
Basic Linux Commands#
- ping: Used to test the connectivity of a remote host(now disabled within NTU network)
- traceroute: Similar to ping , it displays the hops(connections) before reaching the destination
- curl: Used to fetch data from a remote host
- nslookup: Performs a DNS query which returns information about a domain(google.com) such as the IP address of it
- whois: Queries a database which contains the ownership information about the owner of the domain (google.com)
- ssh : Used to establish a secure connection to a remote host, granting access to the command line interface of the host.
