NTU Cybersecurity Club Training Session 2#
What is the Internet?#
The Internet can be seen as a vast network of interconnected devices. Websites are merely other computers showing interfaces for you to interact with
When we consume anything in the internet, its simply just another computer interacting with your own device
Note: Computer simply means a device with the ability to compute and communicate. Even a phone is a computer
https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcTm8K8tMptRebgf1Kseu7kaigT6EqG6dnKDoQ&s
How is the internet connected?#
- Electrical Copper Cables
Common types of cables are RJ45 Cables, which are used commonly in networking. A more common cable is USB Cables
https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcRt7xIMaoVu6tN5471_vI_TxEZolMX7SIm7aw&s
- Fiber Optic
Uses Lasers to pass information via total internal reflection. Fastest and can be extremely long. Expensive.
Many variants available, in the Age of AI where GPU are chained together to train machine learning models, infiniband(fiber optic) is used to ensure the data is passed around GPUs fast enough.


Infiniband
- EM Waves
SatCom technology(StarLink), Bluetooth, Wifi
- Etc New Technologies are created daily
How computer communicate with each other?#
They communicate through packets
Packets
Let’s break down an IP packet structure in a way that’s easy to understand! Think of it like a digital envelope with two main parts:
1. Header (The Envelope)#
- Version (4 bits): Like a postal code format - tells us if it’s IPv4 or IPv6
- Header Length (4 bits): Tells us how long the header is, like the size of the envelope
- Source IP Address (32 bits): Like the return address on an envelope
- Destination IP Address (32 bits): The delivery address where the packet needs to go
- Time to Live (TTL) (8 bits): Like an expiration date - prevents packets from circling forever
- Protocol (8 bits): Indicates what type of data is inside (TCP, UDP, etc.)
2. Payload (The Letter)#
This is the actual data being sent - could be part of an email, a webpage, or any other internet data. The payload can be up to 65,535 bytes!
A fun analogy: If the internet was a postal service:
- The header would be all the information written on the envelope
- The payload would be the actual letter inside
- TTL would be like “please destroy if not delivered within X days”
When you’re browsing websites or sending messages, your data gets split into these packets, each with its own header, and reassembled at the destination - kind of like sending a long letter as multiple postcards!

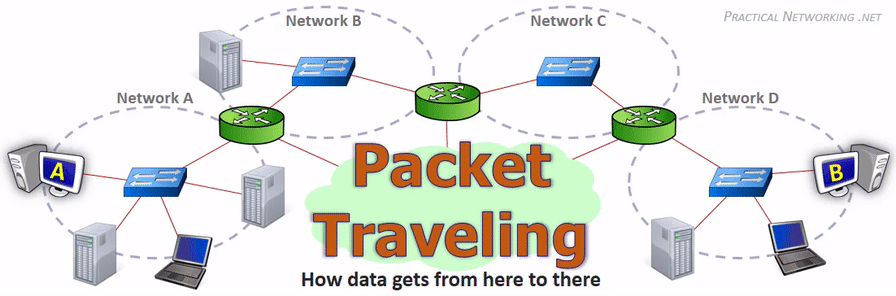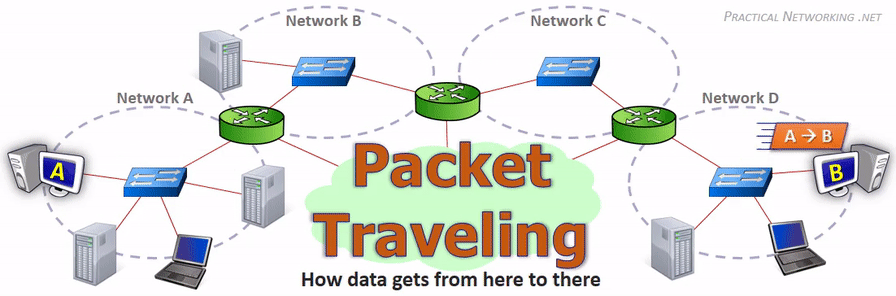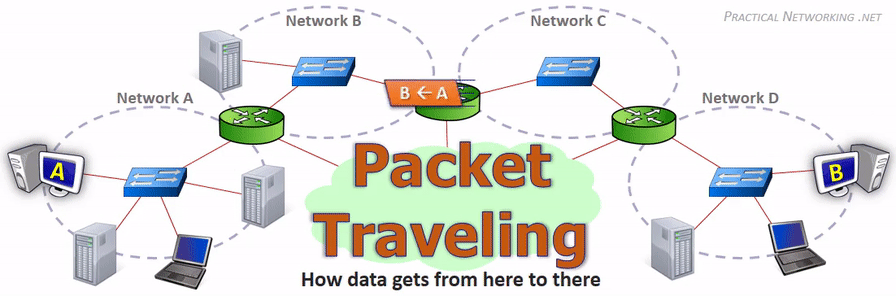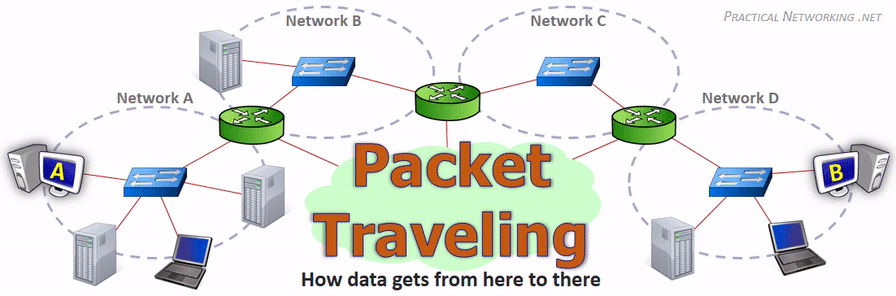
Key Networking Equipment#
- Router: Directs traffic between networks.
- Switch: Connects multiple devices within the same network.
- Firewall: Protects the network by monitoring and controlling traffic.

Router

Switch

Firewall Physical
How can communication channels be attacked: Man In the Middle Attack(MITM)#
A Man in the Middle (MITM) attack is like having someone secretly intercepting and reading letters between you and your friend. In computer networks, it works like this:
Normally: Computer A ↔️ Computer B
With MITM: Computer A ↔️ Attacker ↔️ Computer B
How it works:#
- Interception: The attacker positions themselves between two communicating parties
- Impersonation: They pretend to be the legitimate receiver to both sides
- Data Access: All traffic passes through the attacker, allowing them to:
- Read sensitive information (like passwords)
- Modify data being transmitted
- Insert malicious content
Common Examples:#
- Evil Twin Attack: Setting up a fake WiFi network that looks like a legitimate one (e.g., “Starbucks_Free_WiFi”)
- ARP Spoofing: Tricking devices on a local network to send traffic through the attacker’s computer
- DNS Spoofing: Redirecting web traffic to fake websites that look legitimate
Protection Methods:#
- Always use HTTPS websites (look for the padlock icon)
- Avoid using public WiFi without a VPN
- Keep your system and software updated
- Use strong encryption protocols
Wireshark#
https://www.youtube.com/watch?v=qTaOZrDnMzQ
Picogym questions#
Nice netcat…
Obedient cat
PcapPoisoning
